A hashquine is a enjoyment way to demonstrate off your crypto-methods — It’s a file that has its personal hash. In some file kinds it is trivial, you just pick the hash to hit, and then place random facts in a comment or other invisible field till you get a collision. A Python script that prints its have hash would be uncomplicated. But not every single file variety is so easy. Get PNG for instance. these data files are break up into chunks of knowledge, and each chunk is equally CRC-32 and adler32 checksummed. Make a single transform, and every thing variations, in three destinations at when. Good luck locating that collision. So how specifically did [David Buchanan] generate that gorgeous PNG, which does in actuality md5sum to the price in the image? Quite cleverly.
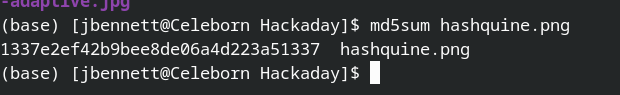
Many thanks to [Julian] for the tip! And as he explained it, this hack is just one that will get much more amazing the much more you imagine about it. Appreciate!

