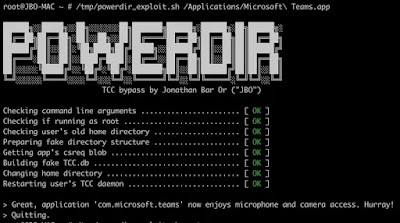
This morning, Microsoft’s 365 Defender analysis group released specifics of a new macOS “Powerdir” vulnerability that makes it possible for an attacker to bypass transparency, consent, and handle technologies to attain unauthorized accessibility to secured facts.
Apple has now preset vulnerability CVE-2021-30970 in the macOS Monterey 12.1 Update released in December, so consumers who have upgraded to the most up-to-date variation of Monterey are secured. Those people who haven’t ought to update. Apple in its Stability Release Notes for Update 12.1 verified the vulnerability of TCC and attributed its discovery to Microsoft.
In accordance to Microsoft, the “Powerdir” safety vulnerability could allow for the installation of a pretend TCC database.
TCC is a very long-lasting macOS function that makes it possible for consumers to configure the privacy options of their apps, and with the pretend database, an attacker could hijack an app mounted on a Mac or put in their very own malicious app by attaining accessibility to the microphone and the digital camera to obtain confidential details.
Microsoft has a in-depth description of how the vulnerability will work, and the firm says its safety scientists keep on to “observe the risk landscape” for new vulnerabilities and attack tactics impacting macOS and other non-Windows units.
“Software package distributors like Apple, safety scientists, and the much larger safety group, have to have to continually do the job together to discover and fix vulnerabilities ahead of attackers can choose edge of them,” wrote Microsoft’s safety group.
